預防仿冒詐騙的保安貼士 (只提供英文版本)
日期: 2018年6月1日
作者: 網絡安全精英嘉許計劃2017金獎得獎者梁國基先生
What Is Phishing Scams?
Phishing scams are actually attempts to trick you into a social networking and fraudulent email message, telephone SMS test message, and instant message from mobile apps. The scammer will spread phishing emails to distribute malicious links or attachments. They usually direct you to a spoofed website to ask your personal details (e.g., passphrase/password, credit card, or other account updates) for malicious reasons, for example, bank account numbers and credit card details for stealing your money or malware embedded in the URL web link. The new trend is that the phishing stoles your computer power and helps the bad guy to mine the cryptocurrency.
Common Features of Phishing Emails
- Too Good To Be True - Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prizes. Just don't click on any suspicious emails. Remember that if it seems too good to be true, it probably is phishing!
- Sense of Urgency - Most phishing emails demand immediate action. Emails saying your account will be deactivated in a day if you don’t enter your credit card number is an example. When in doubt, visit the source directly rather than clicking a link in an email.
- Generic salutation - Phishing emails generally start with “Dear customer” instead of the user’s name.
-
Don’t Trust Your Eyes or URLs -
A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance
www.bankofarnerica.com - the 'm' is actually an 'r' and an 'n', so look carefully.
Phishing emails use various methods to hide the actual URLs.
- The link that is displayed will be an image while the actual link could be different. The bank’s email is not allowed to press the image to link up a link to prevent the wrong URL. The actual URL is not clickable and the user need to type it in their browser software.
- Actual links can be masked using HTML. Thus, the text displayed will be http://websitename.com/ while the hyperlink set will be http://www.othersite.com.
- Another method is by using @ in the link. If a link contains the ‘@’ sign, the URL you’re taken to will be the one after the ‘@’ sign. For example, if the link is www.microsoft.com/windows@web.com/?=true, the actual URL you will be taken to is web.com?=true.
- Links with numbers instead of the website name. Example: www.192.12.24.23.com
- Attachments - If you see an attachment in an email you weren't expecting or that doesn't make sense, don't open it! They often contain payloads like ransomware or other malware.
- Unusual Sender - Whether it looks like it's from someone you don't know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general, don't click on it!
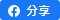
Phishing is popular with cybercriminals, as it is far easier to trick someone into clicking malicious link in a seemingly legitimate phishing email than trying to break through the defenses of a computer. Many of the emails are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren't paying close attention. Figure 1 is one of the typical samples of phishing emails.
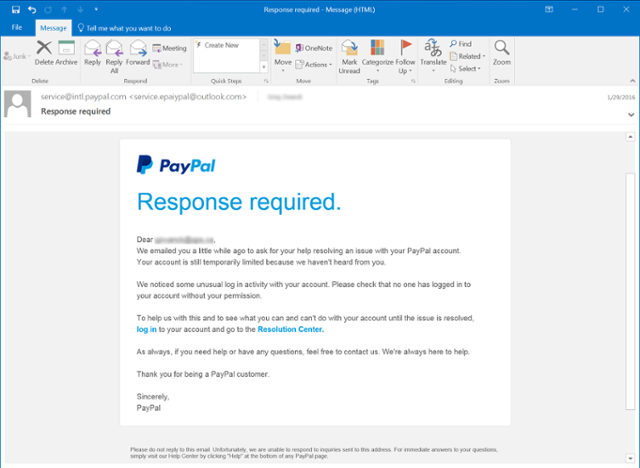
Figure 1
Figure 2 shows the phishing email can be in local language and ask the user to upgrade their email system by clicking a link with malware. This kind of email is simple but effective. Some of these phishing emails are using the name from IT department , even with company logo or with company declaimer.
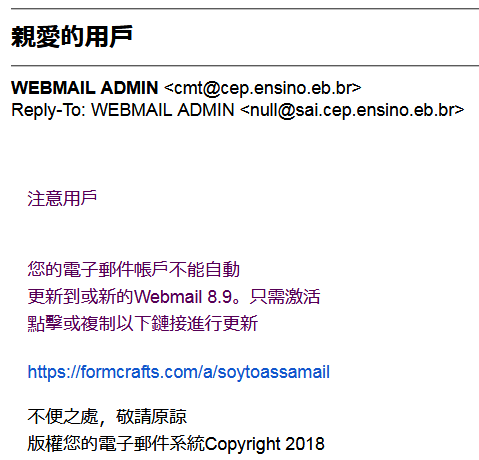
Figure 2
Below is a recent found phishing email (Figure 3) to my email account although I have the spam email filter installed. It claimed that it was coming from Bank of America. We can check the red arrows (Figure 4) how to identify it is a phishing email. The filter rate of Phishing email is various from 80% to 99% among those anti-spam or anti-phishing software or email gateway by different vendors. Using multiple filters may improve the effective filter rate but also increase the false-positive rate i.e., filter the good email as phishing email.

Figure 3
After examining this email, we found the following characteristics so we can identify it is a phishing email.
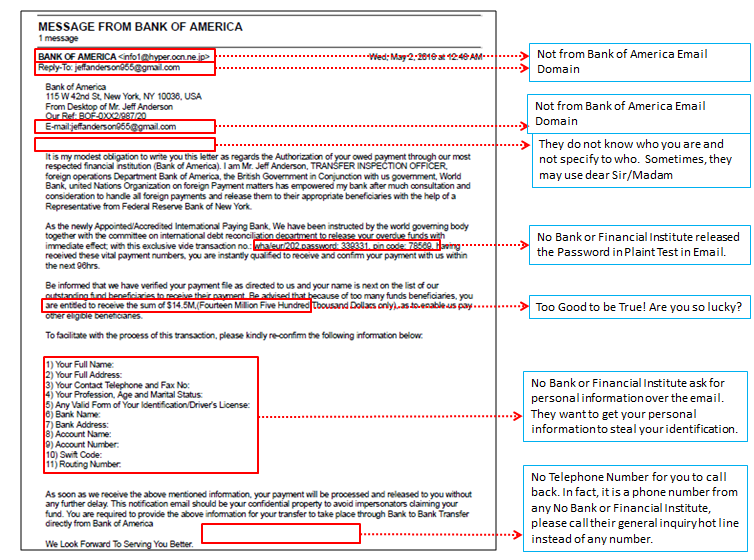
Figure 4
Moreover, you can extract one of the phrases from the email content and paste it into a search engine, it will show you that it is a Phishing Email.
For example, Figure 5 below shows a search engine result by using “It is my modest obligation to write you this letter as regards the Authorization of your owed payment” as the search key words.
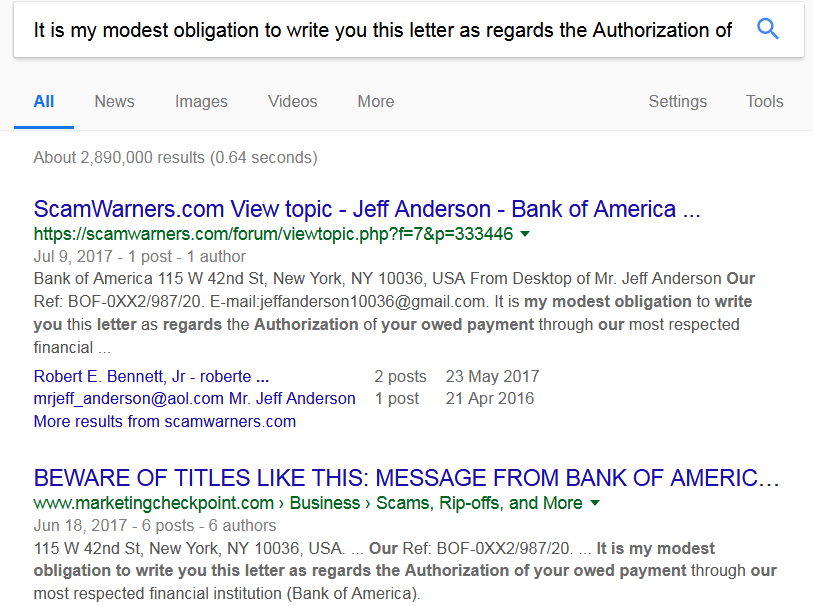
Figure 5
10 Ways To Avoid Phishing Scams
Phishing scams have been around practically since the inception of the Internet, and they will not go away any time soon. Fortunately, there are ways to avoid becoming a victim yourself. Here are 10 basic guidelines in keeping yourself safe:
- Think Before You Click! – A phishing email may claim to be from a legitimate company and when you click the link to the website, it may look exactly like the real website. The email may ask you to fill in the information but the email may not contain your name. It’s fine to click on links when you’re on trusted sites. Clicking on links that appear in random emails and instant messages, however, isn’t such a smart move. Most phishing emails will start with “Dear Customer” or without any attention so you should be alert when you come across these phishing emails. When in doubt, go directly to the source rather than clicking a potentially dangerous link
- Pick Up the Phone to Verify – Do not click on any links or open attachments from emails claiming to be from your bank or another trusted organization and asking you to update or verify your details – just press delete. Never provide your personal, credit card or online account details if you receive a call claiming to be from your bank or any other organization. Instead, ask for their name and contact number and make an independent check with the organization in question before calling back.
- Install an Anti-Phishing Toolbar – Most popular Internet browsers can be customized with anti-phishing toolbars. Such toolbars run quick checks on the sites that you are visiting and compare them to lists of known phishing sites. If you stumble upon a malicious site, the toolbar will alert you about it. This is just one more layer of protection against phishing scams, and it is completely free.
-
Verify a Site’s Security –
It’s natural to be a little wary about supplying sensitive financial information online. As long as you are on a secure website, however, you shouldn’t run into any trouble. Before submitting any information, make sure the site’s URL begins with “https” and there should be a closed lock icon near the address bar. Check for the site’s security certificate as well. If you get a message stating a certain website may contain malicious files, do not open the website. Never download files from suspicious emails or websites. Even search engines may show certain links which may lead users to a phishing webpage which offers low cost products. If the user makes purchases at such a website, the credit card details will be accessed by cybercriminals.
More, you can extract part of the email content or URL link to a search engine, and let the search engine to find the result for you to identify the fake web site or spam email - Effective Anti-Phishing Policies – The company should develop detailed and thorough policies for email, Web, collaboration, social mediaand other tools that are or probably will be used in the foreseeable future. These policies should focus on legal, regulatory and other obligations to encrypt emails and other content if they contain sensitive or confidential data; monitor all communication for malware that is sent to blogs, social media, and other venues; and control the use of personal devices that access corporate systems.
- Be Wary of Pop-Ups – Pop-up windows often masquerade as legitimate components of a website. All too often, though, they are phishing attempts. Many popular browsers allow you to block pop-ups; you can allow them on a case-by-case basis. If one manages to slip through the cracks, don’t click on the “cancel” button; such buttons often lead to phishing sites. Instead, click the small “x” in the upper corner of the window.
-
Never Give Out Personal Information –
As a general rule, you should never share personal or financially sensitive information over the Internet. This rule spans all the way back to the days of America Online, when users had to be warned constantly due to the success of early phishing scams. When in doubt, go visit the main website of the company in question, get their number and give them a call. Most of the phishing emails will direct you to pages where entries for financial or personal information are required. An Internet user should never make confidential entries through the links provided in the emails. Never send an email with sensitive information to anyone. Make it a habit to check the address of the website. A secure website always starts with “https”.
All communications sent over regular HTTP connections are in 'plain text' and can be read by any hacker that manages to break into the connection between your browser and the website. This presents a clear danger if the 'communication' is on an order form and includes your credit card details or social security number. With a HTTPS connection, all communications are securely encrypted. This means that even if somebody managed to break into the connection, they would not be able decrypt any of the data which passes between you and the website. - Keep Your Browser, OS and Apps Up to Date – Security patches are released for popular browsers, OS and Apps all the time. They are released in response to the security loopholes that phishers and other hackers inevitably discover and exploit. If you typically ignore messages about updating your browsers, OS and Apps, stop. The minute an update is available, download and install it.
- Use legal Antivirus Software – There are plenty of reasons to use antivirus software. Special signatures that are included with antivirus software guard against known technology workarounds and loopholes. New viruses are coming out all the time. It is the job of the antivirus software to keep up with the latest threats. This is achieved by daily updates of the antivirus database definitions, which counteract the latest threats to provide constant protection. Today's internet has provided many ways for virus attacks and there are thousands of threats. To be safe from these it is vital to police the computer and have it protected at all times.
- Conduct security awareness training or phishing simulations software. Beside the security awareness, there are phishing/spam simulation and education software to let the company administrator to design the phishing/spam email to their end user. If the end users reacts the phishing/spam email in any incorrect ways, they need to take a training course with quiz or see a phishing/spam educational video. That will help the end user to increase the awareness of the phishing/spam email.
If you suspect that you are a victim of the email scam, please act appropriately according to the following information:
- If you have provided login credentials in suspicious website, please reset password and review the security settings in the related online service accounts.
- If you have provided financial information, such as credit card number, and incur financial loss, please contact your bank immediately.
- You should report to nearby police station if any financial loss is incurred.
- If someone spoofs your identity to send email to your family, friends and business partners, you should alert them by other trusted communication channels.
Phishing scams are very serious threats that can cause enormous damage to an organization’s or individual’s finances, data assets and reputation. They can cause vast disruption to an organization’s employees and IT department, cause an organization to run afoul of industry and governmental regulations, can result in lawsuits, and – in extreme cases – put an organization out of business. For the individuals, their identity may be stolen as well as personal finance lost. However, there are steps that any organization can take to address phishing so that the chances of infection – and the consequences that will arise from it – can be mitigated.
Reference
- http://www.phishing.org/what-is-phishing
- https://www.hkcert.org/my_url/en/guideline/18040602
- http://www.dummies.com/computers/pcs/how-to-recognize-a-phishing-scam/
- https://cdn2.hubspot.net/hubfs/241394/Knowbe4-May2015-PDF/SocialEngineeringRedFlags.pdf?t=1524675334093
- https://www.knowbe4.com/what-is-social-engineering/?hsLang=en&__hstc=59035826.b926b416dc8150c71e54919cb294bee3.1524677217276.1524677217276.1524677217276.1&__hssc=59035826.5.1524677217278&__hsfp=2143943458
- Best Practices for Dealing With Phishing and Ransomware - An Osterman Research White Paper, Published September 2016