端点的多重防御措施 (只提供英文版本)
日期: 2018年7月25日
作者: 网络安全精英嘉许计划2017金奖得奖者罗少辉先生
Organizations should look for an endpoint security solution that can defeat ransomware and other threats regardless of how they attack the endpoints...
Challenges of Securing the Cloud Generation
Today’s workforce is increasingly nomadic. Employees use personal and company-owned devices—desktops, laptops, tablets, and smartphones with various operating systems— to access corporate resources over different networks from virtually anywhere. Roaming users and cloud-based applications have eroded the network perimeter where enterprises have traditionally focused their security controls.
In the wake of this disruption, vendors offered myriad point products that solve only a portion of the security problem. These products usually require costly custom integrations and high management overhead to boot.
Making matters worse, traditional security approaches cannot address an evolving threat landscape that includes ransomware, stealthy attacks that dwell in a customer’s environment 191 days on average (referred to Ponemon 2017 Cost of Data Breach Study: United States), and malware targeting mobile devices. In fact, the mobile workforce is more vulnerable than ever before.
Single-agent Defense in Depth
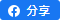
To address the cybersecurity challenges at the endpoint, organizations should find a solution that can secure both enterprise and mobile workforce across traditional and modern OS devices used over any network and from any location. Multiple layers of endpoint security technologies provide you with industry-leading efficacy against emerging threats. The ideal endpoint security solution should work hand in hand with web and email security, threat analytics, security orchestration and automation, and more. A solution that offers single agent architecture and hybrid management capabilities will enable your organization to operate more efficiently and enjoy a lower total cost of ownership.
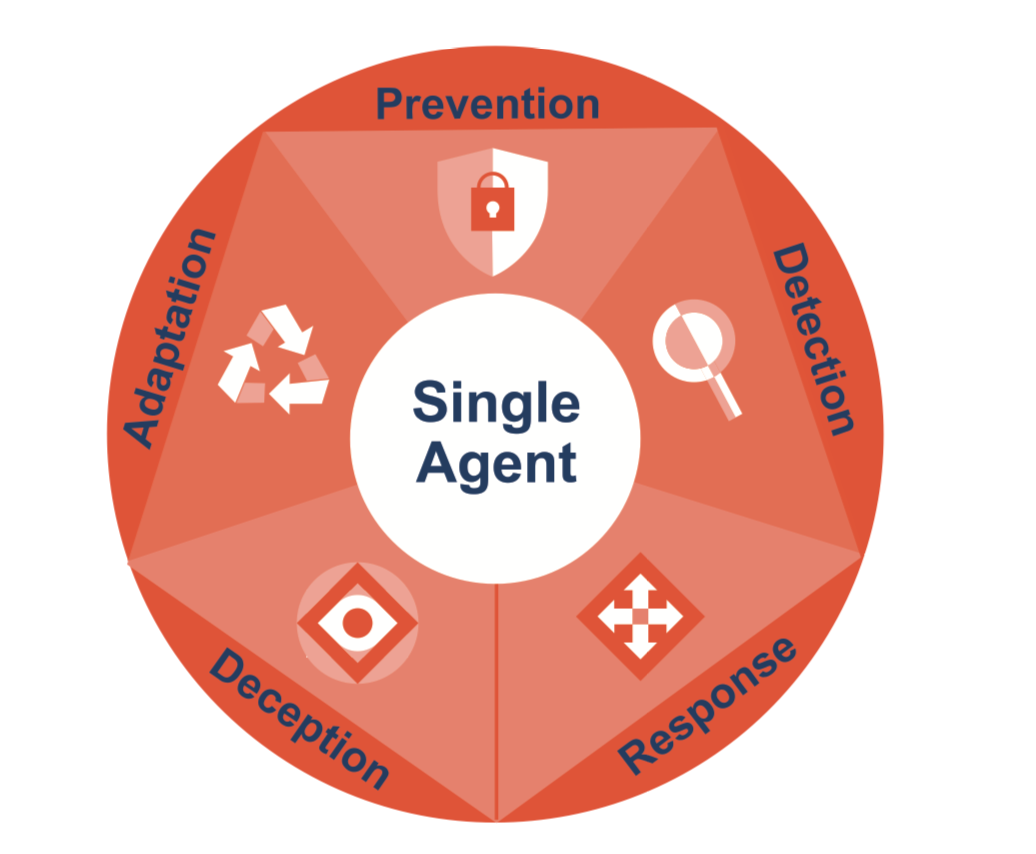
Figure 1: Endpoint security solution with single agent architecture resulting in less management and performance overhead, and a lower overall TCO.
Organizations should look for an endpoint security solution that can defeat ransomware and other threats regardless of how they attack the endpoints. For example:
- Stop ransomware with a combination of artificial intelligence techniques (including advanced machine learning and behavior analysis) and time-tested technologies, such as intrusion prevention. According to the Symantec Internet Security Threat Report Vol. 23, the number of new ransomware variants increased by 46% in 2017, and in addition the WannaCry and Petya/ NotPetya attacks proved that ransomware is a very effective means to infect endpoints and could possibly causing massive damage to the impacted organizations.
- Use signatureless technology to prevent attackers from exploiting vulnerabilities in popular software, including browsers and productivity tools.
- Gain greater visibility into suspicious files, and customize protection on the fly to suit different needs, by fine-tuning machine learning, behavior analysis, intrusion prevention, and more. Use the low-bandwidth mode to protect network- constrained environments without compromising efficacy.
- Orchestrate your response to address threats quickly. Your endpoint security solution should integrate with existing security infrastructure including web and email gateways, sandboxing, and more for a unified threat response.
- Enjoy less operational complexity and a lower total cost of operation by consolidating all endpoint security uses cases— such as prevention, detection and response, deception, endpoint hardening and threat analytics—on a single, lightweight endpoint agent. Such solution will yield higher performance, significantly reducing scan times and bandwidth requirements. Furthermore, the single agent architecture can provide strongest level of protection without compromising user productivity.
Endpoint Detection and Response (EDR) — Intruder Rejection
Sophisticated attackers are increasingly using ‘living off the land’ tactics. One key indicator of this trend is the surge in PowerShell threats: In a Symantec study (Internet Security Threat Report Vol. 22) found that 95.4 percent of PowerShell scripts were malicious. An EDR solution gives you the tools to expose, contain, and resolve breaches resulting from advanced attacks.
The ideal EDR solution should integrate with your endpoint security solution and expose advanced attacks with precision machine learning, behavioral analytics (to detect fileless attacks such as memory-based and malicious PowerShell execution), and threat intelligence—minimizing false positives to help your security team stay productive. Quickly search, identify, and contain all impacted endpoints while investigating threats using on-premises and cloud-based sandboxing. Gain full endpoint visibility and real-time querying ability thanks to the continuous recording of system activity.
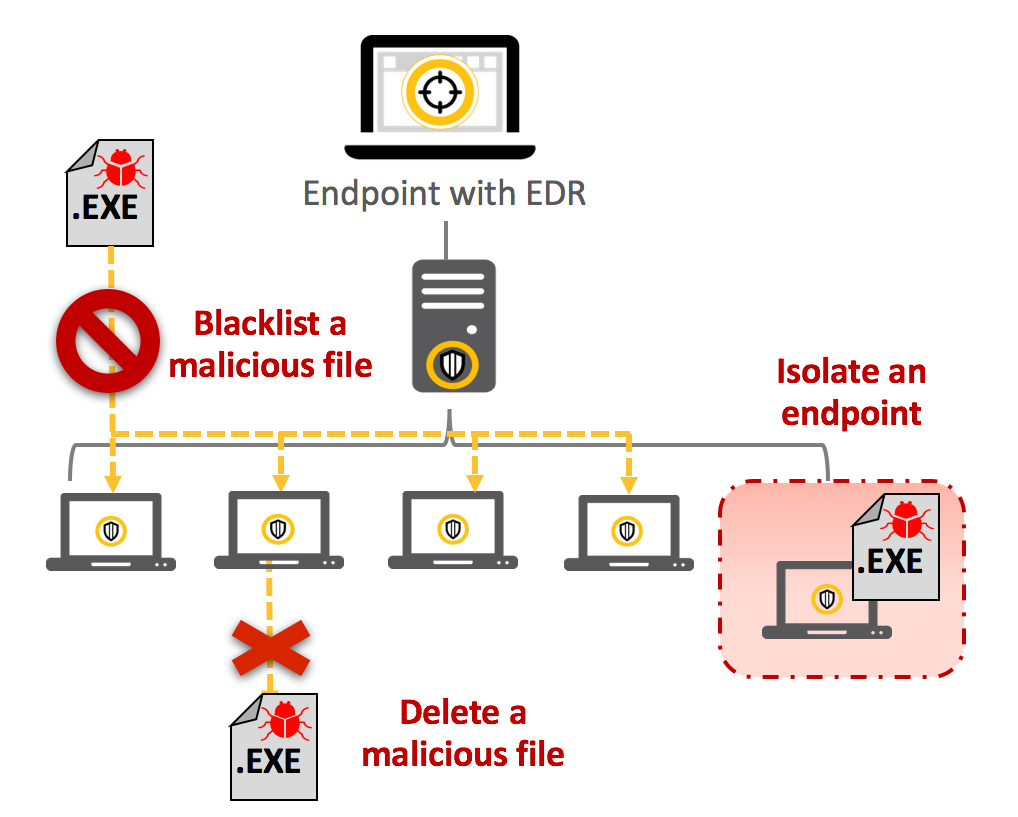
Figure 2: Rapidly fix endpoints with EDR solution.
Organizations Shouldn’t Get Caught Flat-footed
As Symantec Internet Security Threat Report Vol. 23 reported, 1 out of 13 web requests lead to malware and new malware variant which has increased over 87% year over year. Also new malware variants targeting Mac total around 1.4M, about 80% increase year over year. Under this complex threat environment, Symantec recommends organizations to deploy advanced threat detection solution at network, email and endpoint. Also, using next generation endpoint with advanced options (such as AI/ machine learning, sandboxing, IPS, file reputation, behavioural analysis and EDR) turned on helps to detect & block zero-day attack and unknown threats. It is also important to patch endpoints & critical systems with latest update or using virtual patching/ system lockdown solutions to minimize the attack surface.
Besides, people are often the weakest link in a cyber attack so security awareness training, phishing email attack training will help educate users not to download suspicious files or open email attachment with active content or click on phishing web link.