About Beware of Phishing Attacks
Phishing is one of the most common cyber attacks nowadays which targets all Internet and email users. Phishers aim at inducing you to visit malicious websites or to reveal your sensitive information for malicious purposes. To better protect your identity, properties, reputation and computer systems, read on!
 What is phishing?
What is phishing? Common types of phishing
Common types of phishing Risks and impacts
Risks and impacts How to detect?
How to detect? Spot Phishing Emails
Spot Phishing Emails How to avoid?
How to avoid? What to do?
What to do? Videos
Videos Extended readings
Extended readings
What is phishing?
Phishing is the attempt mainly to obtain sensitive information from Internet users by disguising as known individuals or trustworthy institutions such as banks, schools or working partners. In some cases, phishing attacks may infect and compromise computer devices with malware.
Phishing attacks are typically delivered by emails, instant messaging, forged websites or social media. Phishers may attack any time and they often carry out massive phishing campaigns during holidays or in the events of natural disasters, epidemics and major political elections, etc. Internet users should stay vigilant at all times.
Common types of phishing
- Deceptive phishing - Phishers craft messages that look almost identical to those of legitimate institutions or individuals and conduct mass mailings so that recipients might be tricked to give out their sensitive and important personal information.
- Spear phishing - Spear phishing is a more sophisticated version of deceptive phishing. It targets specific individuals or companies. Phishers make use of personal information available from different sources such as social media to craft personalised messages and send them to a selected group or individual, such as senior executives and top management personnel. With a smaller target size, it is easier to include personal information such as the target’s name or job title, making the message seemingly more trustworthy and difficult to be detected.
Risks and impacts
Risks:
- Leakage of sensitive information - Phishers will disguise themselves as known individuals of victims (e.g. victims’ senior management or customers) or trustworthy institutions (e.g. banks) to lure victims to give out their sensitive information such as account names, passwords and identity information. Phishers may further use these sensitive information for malicious purpose or sell them to third parties.
- Malware infection - Links or attachments in phishing emails or phishing websites may contain different malware (e.g. key-logger, ransomware and cryptocurrency mining malware). If users click these links or open these attachments, their devices may get infected by the malware, which may lead to data leakage, data loss or other financial loss.
Impacts:
- Financial loss - With sensitive information obtained from victims, phishers can carry out transactions such as transferring victims’ money to their pockets. Business operations can be disrupted due to the waste of employees’ productivity on handling consequences brought by phishing such as leakage of login account and password.
- Reputational loss - Phishers can further make use of information obtained from victims to send blackmail, intimidate victims’ contacts or even perform illegal activities (e.g. hacking into the system of the victim’s organisation to steal confidential information), causing the victims to be blamed or even get into legal and liability problems. As for an organisation being attacked, it may suffer reputation damage to its brand, and its customers may move their business elsewhere due to losing trust in the organisation in safeguarding their data.
- Intellectual property theft - Intellectual property, including trademarks, patents, trade secrets, etc. is crucial for the success of a company. With the information obtained from victims, phishing attacks can lead to theft of intellectual property which can represent millions or even billions of research and development costs, and may even threaten the future of the company.
How to detect?
Phishing emails:
Phishing emails are crafted like emails sent from legitimate individuals or organisations. They usually contain threats (e.g. suspicious account activities that require immediate actions) or too good to be true offers (e.g. free smartphones). You should stay vigilant when such messages appear in your mailbox.
Common characteristics of phishing emails:
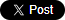
- Intimidating/alarming subject line
- Sent from questionable addresses or public addresses
- Generic greetings
- Ask for personal information
- Grammatical/spelling mistakes
- Links to unrecognised/slightly misspelled sites
Phishing websites:
Phishing websites are usually reached through links from phishing emails, social media or by clicking a suspicious advertisement. The phishing websites usually involve an account login page or a payment page which asks for your sensitive information. Therefore, you should always stay vigilant when visiting such pages.
Common characteristics of phishing websites:
- Forged URLs – Phishing websites often have URLs that are very similar to those of a known organisation, e.g. www.famousorganisation.com vs www.famous-organisation.com.
- Address begins with HTTP – You should only submit your sensitive information through a HTTPS website, instead of a HTTP website.
- Low quality – Phishing websites are often created rashly with a short life cycle, thus grammatical/spelling mistakes and low resolution images are sometimes observed.
- Ask for personal information – Phishing websites are created to lure you into giving out your personal information or credentials.
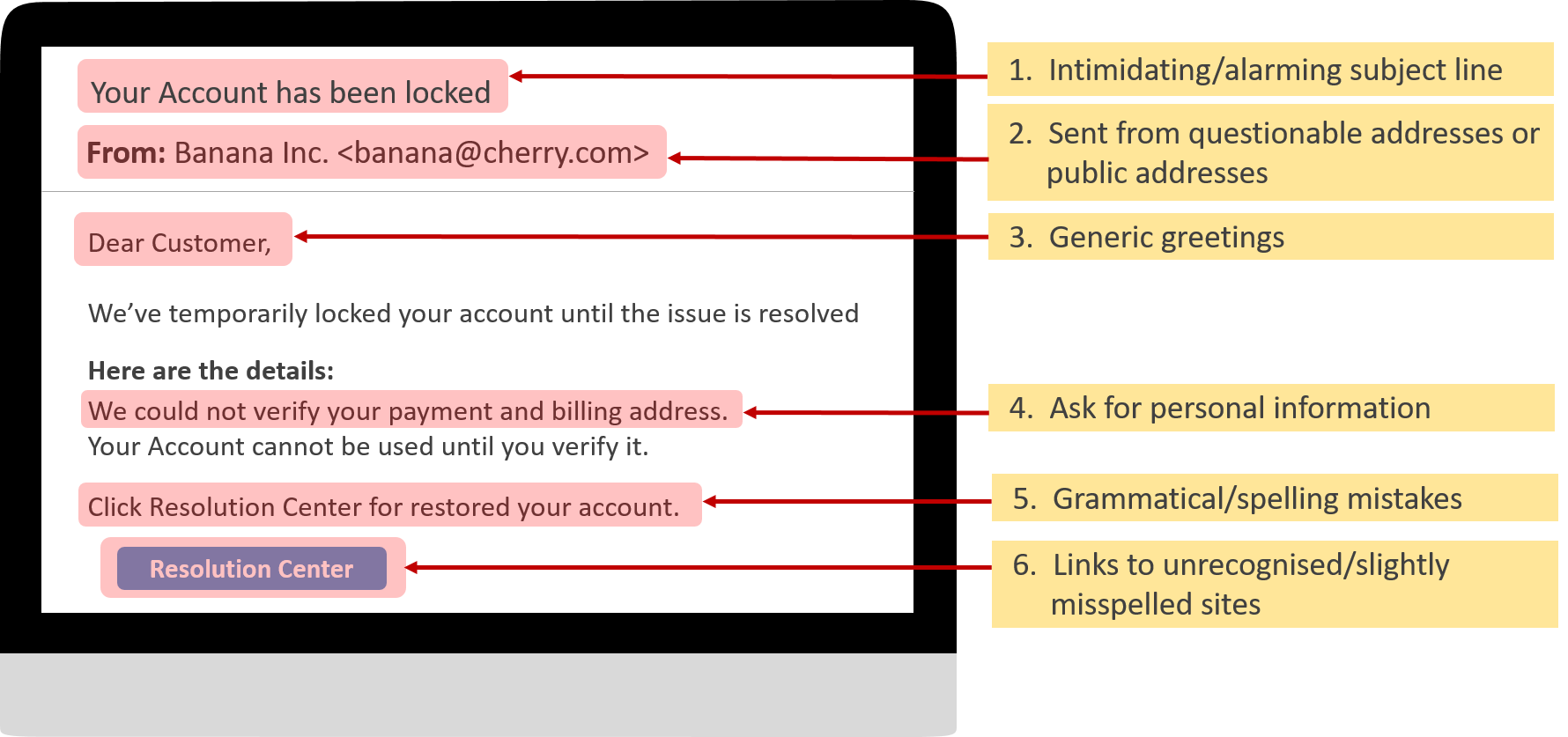
Example of a phishing website:
- No padlock sign (shows the "Dangerous" sign)
- Use HTTP instead of HTTPS
- Domain is "bemoepay" instead of "demoepay"
- Ask for credentials
Spot Phishing Emails
Phishing emails can bring about serious security risks. They will steal your personal information and also infect your computers. Phishing attacks affect not only your computer but may also use your computer to compromise other computer systems of your organisation.
(The challenges include four sample emails. Please try to identify these emails as “Genuine” or “Phishing”.)
How to avoid?
Internet users:
While using email services
- Always stay vigilant to suspicious emails.
- Do not open any suspicious emails.
- Always check email attachments’ extension – Open email attachments with extreme care. Never open an attachment with “pif”, “exe”, “bat”, “cmd”, “vbs” extension.
- Always stay vigilant when giving out sensitive personal or account information – Banks and financial institutions seldom ask for your personal or account information through emails. Check with the relevant organisations in case of doubt.
While browsing the Internet
- Avoid following links - Never follow URL links from un-trusted sources, emails or social media. Do not rely on search engine results without verifying the validity of websites of banking or financial institutions.
- Type URLs manually or use bookmarks for frequently visited websites or financial institution websites.
- Do not visit suspicious websites.
- Avoid conducting online banking using public WiFi connections, public terminals or insecure terminals such as those in cafés or libraries.
While using social media platforms
- Do not accept friend-making requests from people you do not know - Once someone becomes your friend on the social media, he can access your information such as your profile, photos and social activities records. Such information may be used for illegal purposes such as spear phishing.
- Limit the amount of personal information available in your profile – Avoid including sensitive information such as your home address in your profile. Always remember the more information you include in your profile, the higher are the risks of leaking such information to strangers.
- Carefully configure your privacy settings – Decide very carefully what information you wish to make public or what to keep to your friends only.
Other security considerations
- Update security patches and virus signatures - Always ensure that the security patches and virus signatures on your computer are up-to-date.
- Deploy spam filter software – Consider using desktop spam-filtering products and browser’s built-in functions to help detect and block fraudulent emails but beware of false alarms.
For organisations:
- Inform users of the preventive measures implemented by your organisation – For example, your organisation will not ask for users’ personal or account information through email or by phone.
- Keep your website certificates up-to-date - Users can be assured the legitimacy of the websites.
- Provide channels for users to verify and report any suspicious emails/websites.
- Register similar domain names - Consider registering domain names that are similar to the one that is currently used by your organisation. For example, in addition to the original domain name “www.aaaabank.com.hk”, domain names “www.aaaabank.com”, “www.aaaabank.hk” can also be registered.
- Strengthen the security controls of your organisation’s websites, applications and email systems – Consider deploying technological solutions such as Secure Sockets Layer (SSL), two-factor authentication, digital certificates, firewalls and anti-malware solutions. You may also consider implementing email authentication protocols such as Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). The SPF can help ensure that the email is sent by the sender it claims while DKIM can help verify that the content of the email is not tampered.
- Strengthen your operational controls - For financial institutions, implement policies such as setting limits on users’ maximum daily transaction amount, requesting pre-registration of users for using certain online transaction services.
- Educate users - Develop a set of best practices for users to follow when using Internet services.
- Conduct anti-phishing training/simulation tests regularly.
What to do?
When you receive suspicious email messages:
-
Do not click on any links or download any attachments

The links might lead you to malicious websites while the attachments might contain malware.
-
Do not reply to the email

Report to appropriate parties such as your organisation’s network administrator promptly for checking and cleansing.
-
Check the true destination of links

Hover over the link to check the destination address and scan it with a link scanner such as Norton SafeWeb, URLVoid, or VirusTotal.
-
Verify the sender

Verify the sender through channels other than those stated in the email, e.g. phone numbers found on your credit card or statement.
-
Delete the suspicious messages

Delete the message if you are confident enough that it is spam.
-
Report to appropriate parties

Report to appropriate parties, e.g. your bank. You should also consider reporting the attack to the Hong Kong Police Force if necessary.
When you click on a link or download attachments in a suspicious email:
-
Disconnect your device from the network

This can reduce the risk of spreading malware to other devices on your network and prevent malware from sending sensitive information from your device.
-
Report immediately

Report to appropriate parties such as your organisation’s network administrator promptly for checking and cleansing.
-
Perform a malware scan

Before reconnecting your device to the network, run a complete scan with your anti-malware software. Follow the instructions given by the software to remove any suspicious files found.
-
Change your credentials

Malware may have already harvested your credentials for online accounts such as email, online banking and social media. You should change your online credentials immediately to stop phishers from using your accounts.
When you have provided sensitive information to phishing emails/websites:
-
Change your credentials

Change your passwords for the related accounts.
-
Report immediately

Report to appropriate parties, e.g. your bank or your organisation’s network administrators. You should also consider reporting the attack to the Hong Kong Police Force.
When my organisation’s identity is being used in a phishing attack:
-
Alert users

Issue prompt alerts to users, related parties or even the public through press release, website or emails about the fraudulent website and warn them not to respond to the suspicious or phishing emails.
-
Report immediately

Report to the police and relevant organisations or regulatory bodies such as the Hong Kong Monetary Authority about the suspicious website.
-
Advise potential defrauded users

Advise users who are suspected to be defrauded to change their passwords immediately and report to the police if necessary.
-
Alert your website administrators

Issue alerts to staff, administrators or service providers of your organisation’s website to strengthen security measures and to watch out for any suspicious activities such as suspicious port scanning activities, abnormally high traffic volume, or connections to suspicious servers on the Internet.
Videos
Extended readings
- Cyber Security Information Portal – Tips on Protection against Phishing Scam
- Phishing.org – 10 Ways To Avoid Phishing Scams
- US-CERT – Avoiding Social Engineering and Phishing Attacks
- HKMA – Sample Phishing Emails Purportedly from Banks
- HKMA – Smart Tips Against Phishing Emails
Disclaimer: Users are also recommended to observe the Important Notices of this website and read the user agreements and privacy policies of the security software and tools before download and use them.