Introduction
Ransomware is a malicious software that cyber criminals used to lock the files stored on the infected computer devices. These locked files are like hostage and the victims are required to follow the instructions of this malicious software and pay a ransom to unlock them.
Security Tips to Effectively Defend Against Ransomware
- Perform regular backups on important data and keep the backup copies disconnected from the computer
- Install the latest patches for operating systems and software in use
- Keep your anti-malware program and signatures up-to-date
- Schedule a regular full scan to detect and guard against malware attacks
- Do not open any suspicious emails or instant messages, as well as the attachments and hyperlinks inside
- Refrain from visiting suspicious websites or downloading any files from them
 Causes and Impact
Causes and Impact Screenshots of Infection
Screenshots of Infection Preventive Measures
Preventive Measures What Should I Do if Infected?
What Should I Do if Infected? Reference Tools on Decryption
Reference Tools on Decryption Videos
Videos Infographics
Infographics Extended Readings
Extended Readings
Causes of Infection and Impact
Causes of Infection
- Open suspicious emails, or attachments and hyperlinks inside
- Visit websites embedded with malicious programs
- Download and install software or mobile apps that are embedded with ransomware
Impact
- Files inside the computing device and other connected storage devices are locked. These data would be lost unless timely backup is available.
Screenshots of Ransomware Infection
The following screenshots illustrate the stages of a computer being infected by a ransomware. It should be noted that different ransomware will have different behaviour.
7 stages of a computer being infected by a ransomware
-
Step 1 of 7: Files with known extension on a computer before infected by ransomware
-
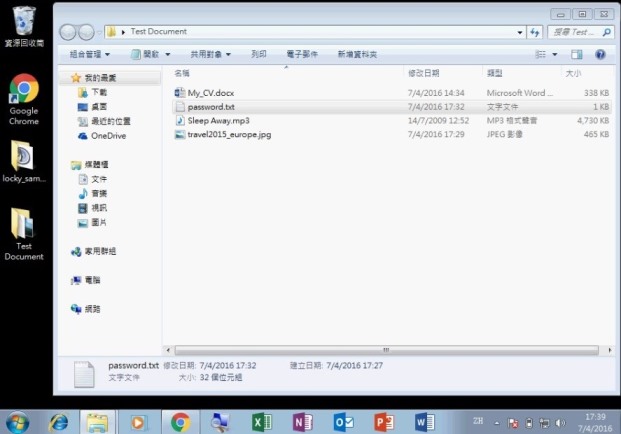
Step 2 of 7: The user opens a program embedded with ransomware
-
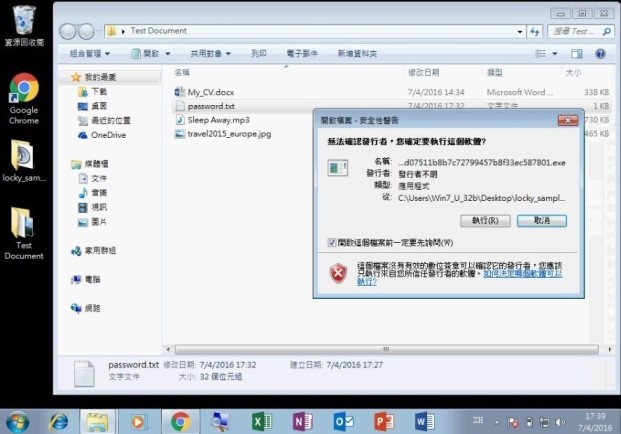
Step 3 of 7: The ransomware starts to encrypt the files inside the computing device
-
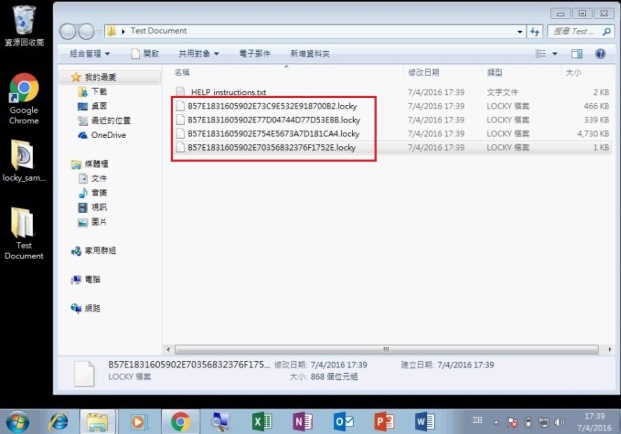
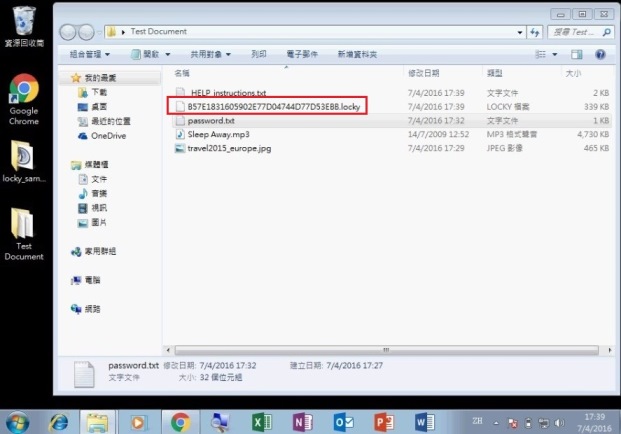
Step 4 of 7: All documents, photos and media files are encrypted by ransomware
-
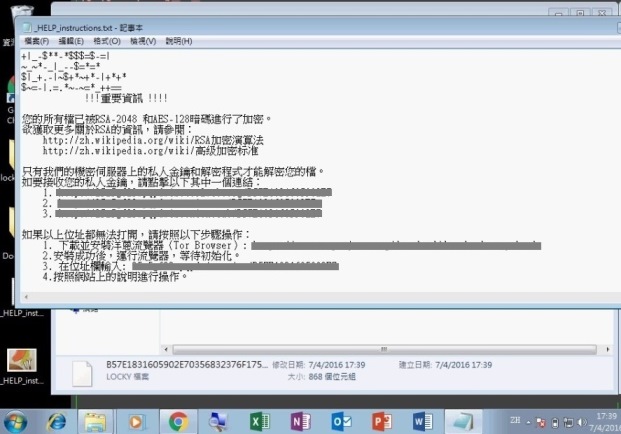
Step 5 of 7: A text file is created telling that the files inside have been encrypted
-
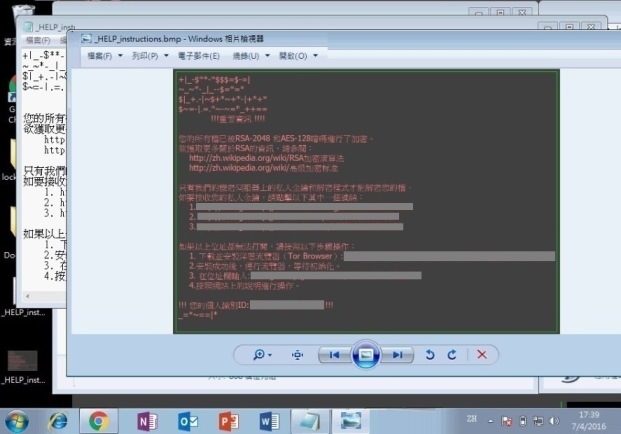
Step 6 of 7: A graphic file is also created and informs the user of the same content
-
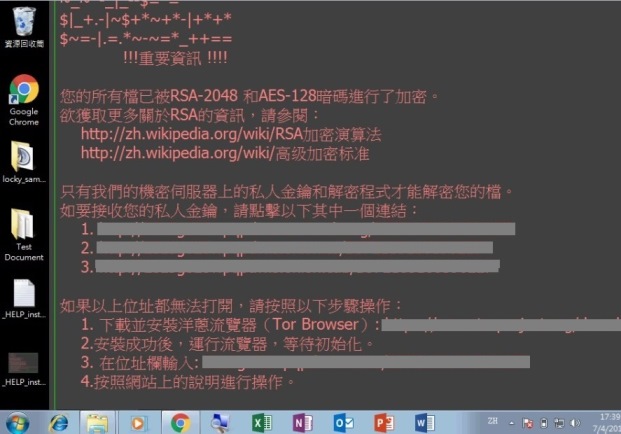
Step 7 of 7: The wallpaper is changed at last
Preventive Measures
Preventive Measures
- Perform regular backups on important data and keep the backup copies disconnected from the computer
- Install the latest patches for operating systems and software in use
- Apply least privilege principles to all systems and services
- Keep your anti-malware program and signatures up-to-date
- Enable firewall protection
- Schedule a regular full scan to detect and guard against malware attacks
- Disable or restrict all unnecessary services and functions such as Remote Desktop Service (RDP) in computer systems
- Disable all unnecessary ports such as SMB ports (TCP ports 139 and 445) from Internet access
- Disable macros for Microsoft Word, Excel and other office applications by default
- Do not open any suspicious emails or instant messages, as well as the attachments and hyperlinks inside
- Refrain from visiting suspicious websites or downloading any files from them
- Install software and mobile apps from trusted sources, do not install those apps if suspicious permission rights are required
- For business operations with a higher risk of exposure to malware infection such as customer enquiry emails handling, a dedicated computer with no network drives and restricted network connectivity to internal network should be used to minimise the impact of infection and the handling staff should keep alert of possible infection
Anti-malware security software
What Should I Do if Infected?
- Disconnect the network cable of the computer to avoid affecting network drives and other computers
- Power off the computer to stop the ransomware from encrypting more files
- Jot down what have been accessed (such as programs, files, emails and websites) before discovering the issue
- Report to the Hong Kong Police Force for technology crime
- Recover the data from backup to a clean computing device
Reference Tools on Decryption
You may check if there is any reference tools to recover the encrypted files. Apart from the below reference tools, you could also visit the “The No More Ransom Project” and ID Ransomware (a free website that helps victims identify what ransomware may have encrypted their files) websites to check whether there is a solution available for the infected files.
Videos
Infographics
Extended Readings and Other Resources
- Cyber Security Information Portal - Learning Centre, Beware of Malware Infection
- Cyber Security Information Portal - Precious Photos Encrypted by an Email? (Chinese Version Only)
- Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) - Fight Ransomware
- Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) - Security Blog, Beware of Crypto Ransomware
- Hong Kong Police Force - CyberDefender - Ransomware
- InfoSec website - Protecting against Malware
- InfoSec website - Malware
- SingCERT - Protect Your Systems and Data From Ransomware Attacks
- “The No More Ransom Project”
- US-CERT - DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks
Disclaimer: Users are also recommended to observe the Important Notices of this website and read the user agreements and privacy policies of the security software and tools before download and use them.