- 1
 Application restriction
Application restriction - 2
 Screen lock
Screen lock - 3
 Anti-malware tool
Anti-malware tool - 4
 Software update
Software update - 5
 Device encryption
Device encryption - 6
 Wi-Fi connection
Wi-Fi connection - 7
 Location services
Location services - 8
 Application permissions
Application permissions - 9
 Device backup
Device backup - 10
 Remove information
Remove information
 Restrict Installation of Applications from Unknown Sources
Restrict Installation of Applications from Unknown Sources

RISK

Mobile applications distributed from unknown sources have higher risk to contain malicious codes.
CHECK STEPS
iOS users can protect their mobile device from unknown source software by not "jailbreaking" the device. iOS only allows installation of mobile application via the official Apple App Store or the Apple's code signing mechanism.
You can identify jailbroken iOS device by manual check -
- Search for common apps, such as "Cydia" and "Icy" that are installed after jailbreaking.
- Verify whether any default iOS apps are missing because default apps can be uninstalled on jailbroken iOS device only.
MORE TIPS
- Recover jailbroken device by making reference to the official Apple website on Use iTunes to Restore Your iOS Device to Factory Settings.
 Set Strong Password and Screen Lock
Set Strong Password and Screen Lock

RISK

Unauthorised person can access information in an unlocked mobile device without the owner's knowledge.
CHECK STEPS
System settings
Purpose: Enable alphanumeric password protection and screen lock -
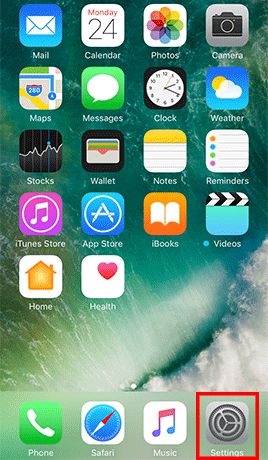
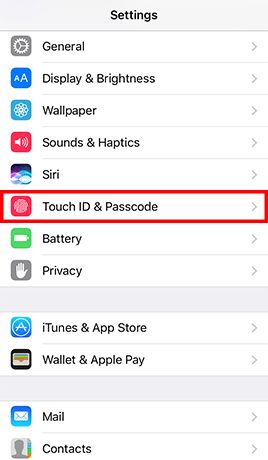
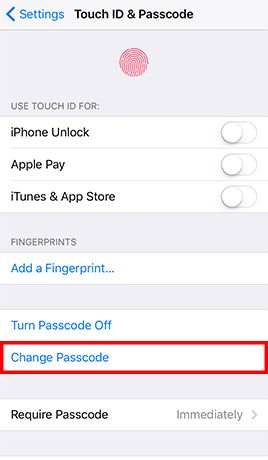
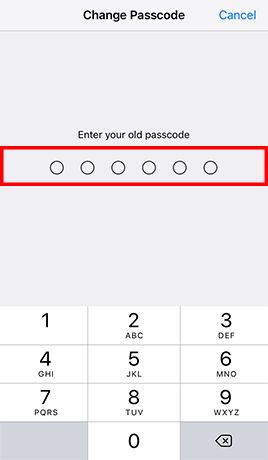
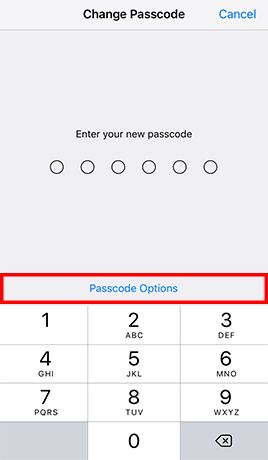
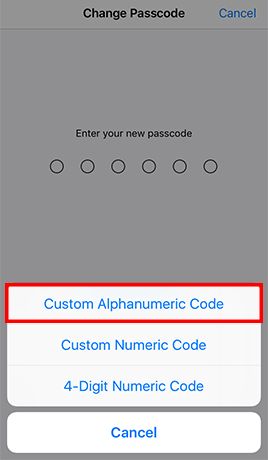
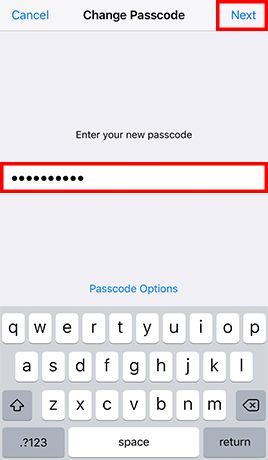
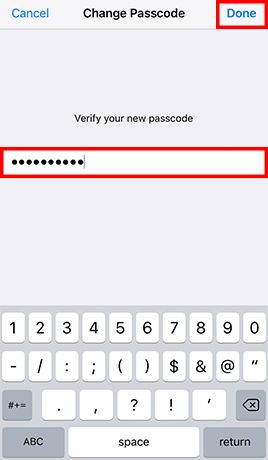
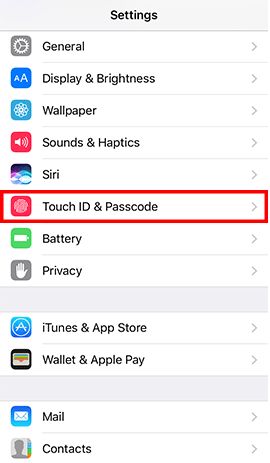
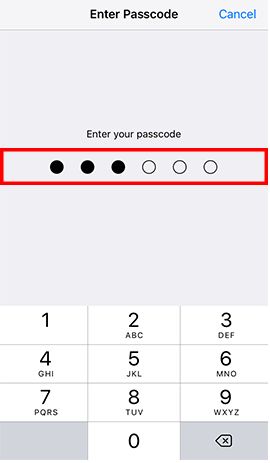
- Step 1: Go to Settings -> Tap Touch ID & Passcode and enter the current passcode if configured -> and enter your old passcode when prompted -> Tap Passcode Options and Choose Custom Alphanumeric Code -> Enter a strong password and tap Next -> Re-enter the password and tap Done
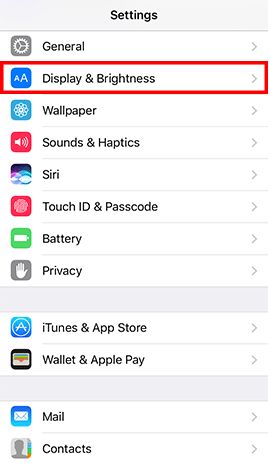
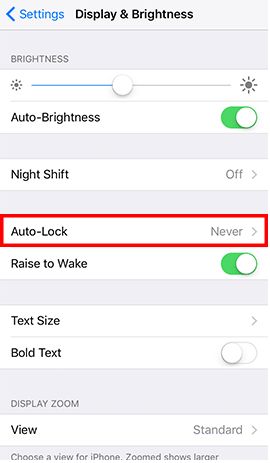
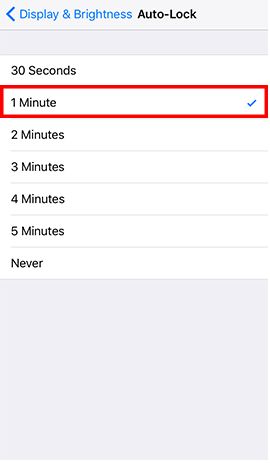
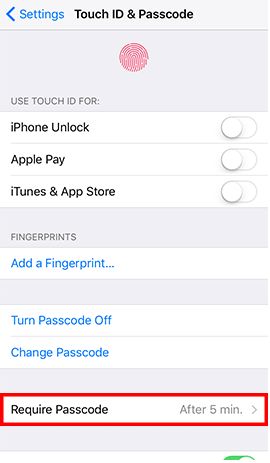
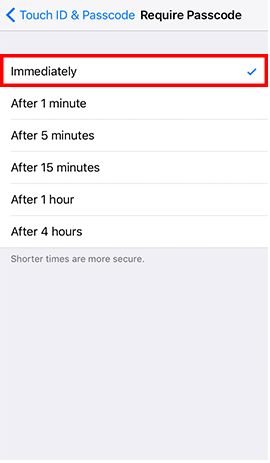
- Step 2: Go to Settings and tap Display & Brightness -> Tap Auto-Lock -> Tap 1 Minute -> Back to Settings -> Tap Touch ID & Passcode and enter the password -> Tap Require Passcode -> Tap Immediately
MORE TIPS
- Set strong password instead of 4 digit passcode for better security, as simple passcode could be easier to guess and trivially peeked by someone around you.
- Create passwords that are easy for you to remember but difficult for others to guess, with assistance of free online tools to learn and practice.
- Don't leave your mobile device unattended.
 Use Up-to-date Anti-malware Security Software
Use Up-to-date Anti-malware Security Software

RISK

Mobile applications and files that look innocent can contain malicious codes and may not be easily noticed by user before it causes significant damages.
CHECK STEPS
iOS users can protect their mobile device from malware attack by not "jailbreaking" the device. iOS only allows installation of mobile application that has been approved by Apple. Apple reviews all applications in the official Apple App Store to filter out malicious software, so the risk of encountering malware on iOS device would be low.
Note: In general, no security tool can perform full anti-malware scan on all files in an iOS device because Apple has enforced a process called sandboxing to prevent third party applications from accessing other application files or making changes to the device.
MORE TIPS
- Stay alert to symptoms that might indicate a malware infection, such as battery drain, performance clogging, unusual large data usage, etc.
- Be aware that fake anti-malware software and rogue pop-up security alerts are popular ways for tricking users to download malware onto their devices.
 Update Operating Systems, Mobile Applications and Browsers
Update Operating Systems, Mobile Applications and Browsers

RISK

Mobile devices with known security weaknesses are more susceptible to malware infection and other cyber attacks.
CHECK STEPS
Tool(s) available
Function: Detect outdated iOS, browser and program in mobile device.
- iTunes / Over-the-air (Check for iOS updates)
System settings
Purpose: Enable automatic update of mobile application.
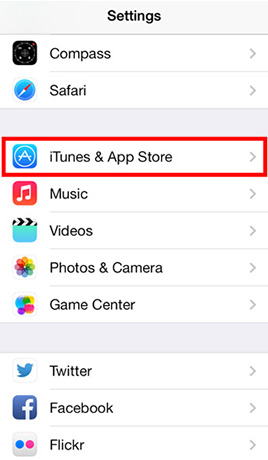
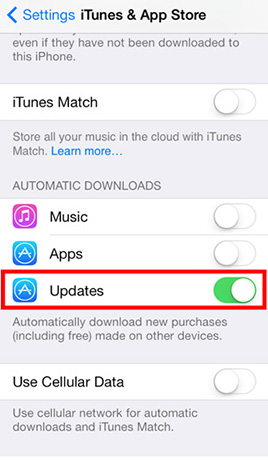
Tap Settings and then tap iTunes & App Store -> Turn on Updates in the Automatic Downloads configuration listMORE TIPS
- Uninstall end-of-support software products or upgrade to another software product that has security updates.
- Avoid performing sensitive operations, such as online banking, from a mobile device without security updates, as not all iOS devices will support the most recent version of iOS.
- Do not visit suspicious websites or follow the links provided in those websites, as they may force a browser to download files without user's knowledge.
 Encrypt Your Mobile Device
Encrypt Your Mobile Device

RISK

Data in a mobile device can be leaked out, if it is lost or stolen.
CHECK STEPS
By default, data encryption is already enabled for iPhone 3GS and later, and for all iPad models. However, you are advised to further secure your iOS device by protecting the encryption key with a strong password.
MORE TIPS
- Use Find My iPhone feature that allows you to remotely track, lock or erase your iOS device in case it is lost or stolen.
 Remove Insecure and Unnecessary Wi-Fi Connection Profile
Remove Insecure and Unnecessary Wi-Fi Connection Profile

RISK

Mobile devices with insecure Wi-Fi connection profile have higher risks to join untrusted or spoofed Wi-Fi networks automatically.
CHECK STEPS
System settings
Purpose: Remove Wi-Fi network profile and disallow iOS device to rejoin remembered Wi-Fi network automatically.
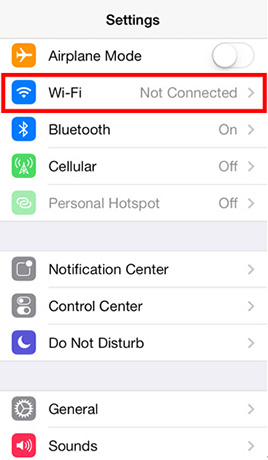
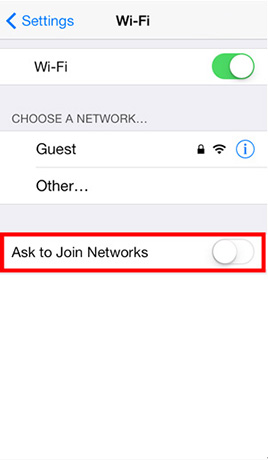
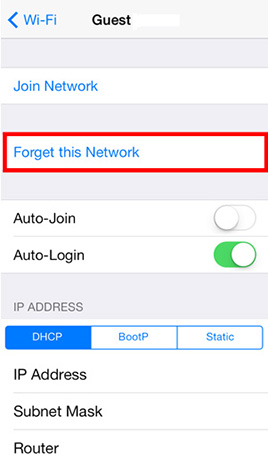
- Step 1: Tap Settings and then tap Wi-Fi -> Turn off Ask to Join Networks
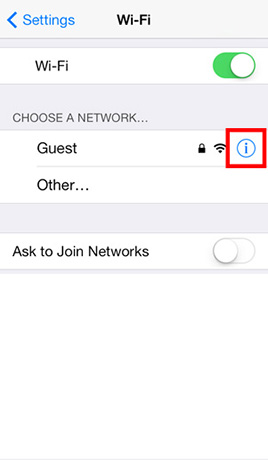
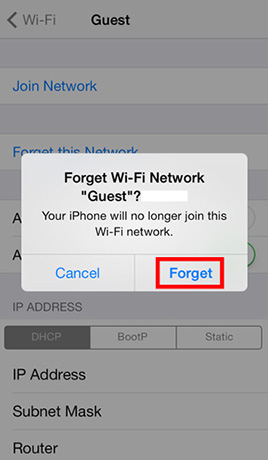
- Step 2: Locate the Wi-Fi network to forget and tap the Detail Disclosure button -> Tap Forget this network -> Tap Forget
Note: The Wi-Fi network must be in range for it to appear in the list of available networks to forget. If the Wi-Fi network is no longer in range, the user must reset all network settings, which will forget all Wi-Fi networks.
MORE TIPS
- Avoid handling personal or sensitive information when using public Wi-Fi
- Disable wireless connection after use.
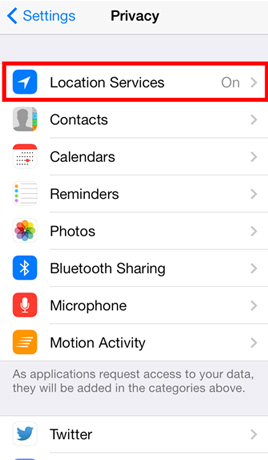
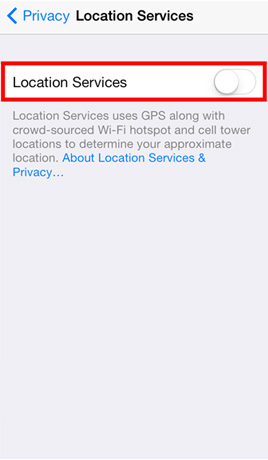
 Disable GPS and Location Services
Disable GPS and Location Services

RISK

Mobile device allow installed applications and visited websites the ability to know and track user location without users’ knowledge.
CHECK STEPS
MORE TIPS
- Remove applications required location tracking, if no operational needs.
- Disable GPS function and location services after use.
 Remove Mobile Applications that Abuse Sensitive Permissions
Remove Mobile Applications that Abuse Sensitive Permissions

RISK

Mobile applications, obtained sensitive permissions can perform high risk actions without user knowledge, such as enable camera and send SMS.
CHECK STEPS
iOS users can protect their mobile device from risky mobile applications by not “jailbreaking” the device and only downloading mobile applications from official Apple App Store. iOS has enforced a process called sandboxing to prevent third party applications from accessing other application files or making system changes. Moreover, Apple reviews all mobile applications in the official Apple App Store to filter out malicious software, so the risk of encountering high risk applications on iOS device would be low.
MORE TIPS
- Before installation, research for whether the mobile application is reputable by researching via public search engine using the application name with other keywords for example "review", "complaints", "compare", etc.
 Perform Device Backup
Perform Device Backup

RISK

Data cannot be recovered in case of malware infection, hardware failure and device loss.
CHECK STEPS
Tool(s) available
Function: Backup data in mobile device to your computer and restore data.
Note: For better security, you are recommended to protect your backup using the Encrypt Backup option with a strong password.
MORE TIPS
- Backup regularly and protect your backup data securely.
- Test the restore procedures to ensure the backup data can be restored.
- Assess security risks before synchronising data to cloud services and avoid automatic backup of sensitive data to them.
- Protect your online user account with a strong password and enhanced authentication mechanism such as 2-factor authentication if available, in particular those for cloud backup. Please visit InfoSec website for more good practices on Handling User Account and Passwords.
 Remove Personal Information before Giving Away or Selling Your iOS Device
Remove Personal Information before Giving Away or Selling Your iOS Device

RISK

Your personal information can be accessed if the data was not removed properly.
CHECK STEPS
System settings
Purpose: Backup the device, logout the cloud service, and erase the content and settings.
- Steps on how to remove your personal information from an iOS device
MORE TIPS
- You may make reference to the vendor's webpage for transferring content from a current iOS device to a new iOS device.
Disclaimer: The health check settings here are proactive in nature and intended for improving mobile device security, as they may change the user experience and interfere with the functionality and utility of some applications. The exact process for applying the security features during the health check will vary between different products. It is recommended to follow the instructions contained in the user manual provided at the official website of the manufacturer where possible.
Users are also recommended to observe the Important Notices of CSIP and read the user agreements and privacy policies of the security software and tools before download and use them.