Offensive AI: How you can optimize your Cybersecurity investment to prevent and detect attacks with AI technologies
Date: 31-March-2022
Organisation: Deloitte Advisory (Hong Kong) Limited
Writer: Ms. Eva KWOK, Mr. Terence LI and Ms. Vanessa MAK
After a few decades of rapid growth of Artificial Intelligence (AI) since 1950, AI has a greater and broader relevance to human lives. In the cyber world, the development of AI has enabled a wide range of beneficial applications, such as automated speech recognition (like Apple's Siri and Google's Alexa), AI-driven chatbots and search engines. At the same time, attackers are turning to AI to weaponize advanced malware and attacks, to increase the target coverage, attack speed and the chance of successful compromise.
What are the common usages of offensive AI?
Attackers commonly employ AI for more tailored impersonations, and quicker intrusions with more sophistication and automation.
Impersonations
Offensive AI via impersonation increases the effectiveness of exploiting human behavior, commonly the weakest link in cyber security.
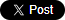
- AI-generated phishing emails. Researchers found that AI could write better phishing emails than humans. Deep learning language models like GPT-3, along with other AI-as-a-service platforms significantly lower the barrier to craft effective and targeted phishing message.
- AI voice impersonation. With deep learning, criminal can perform highly effective spear phishing attacks by impersonating a superior's voice to convince the company employees to carry out malicious activities.
- Deepfake personas. Attackers leverage deepfakes to dupe biometric authentication while verifying a human identity, and to compromise business email and business communication platforms (like MS Teams, Zoom).
Intrusions
Besides, criminals use offensive AI to exploit and penetrate into company systems and evade security intrusion detection.
- AI captcha bypass. CAPTCHAs were designed to prevent computers from automatically filling out forms by verifying that you are a real person. But with the rise of deep learning and computer vision, machines are trained to defeat CAPTCHAs automatically to enable credential stuffing attacks and brute force attempts.
- AI fuzzing. AI can be leveraged to speed up the discovery of zero-day vulnerabilities, automated reverse engineering and exploitation of side channels.
- AI-controlled bot. AI can help criminals to improve stealth capabilities by using automation to perform lateral movement across networks to infect more machines.
Figure 1: common AI-powered attacks types
Are organizations ready for that?
In 2021, MIT Technology Review Insights and Darktrace conducted a survey with 300+ C-level executives, directors, and managers worldwide to understand how they are addressing the cyber threats they are up against [Note 1]. It is noted that 60% of respondents reporting human-driven responses to cyberattacks are failing to keep up with automated attacks. When survey respondents were asked how worried they are that future cyberattacks against their companies will use AI, 97% cited future AI-enhanced attacks as troubling, with 58% of respondents saying such cyberattacks are very concerning.
Mainstreaming AI-driven attacks is just a matter of time. In addition, the trend of digitalization and COVID-19 pandemic have significantly increased the complexity of cyber battlefield. It is not uncommon to see organizations invest millions to buy various tools and hire security professionals to protect against cyber attacks. However, it remains a traditional and reactive approach that does not prevent AI-driven attacks. It is time to start adopting AI technologies to help effectively and efficiently prevent and detect attacks.
Where can we start?
Your organization is a treasure trove full of data and information collected from various systems you may have already installed to prevent cyber attacks. Based on your current capabilities, you can identify specific areas where AI technologies and cyber analytics can be applied. The framework is depicted as a table that spans all phases of cybersecurity.
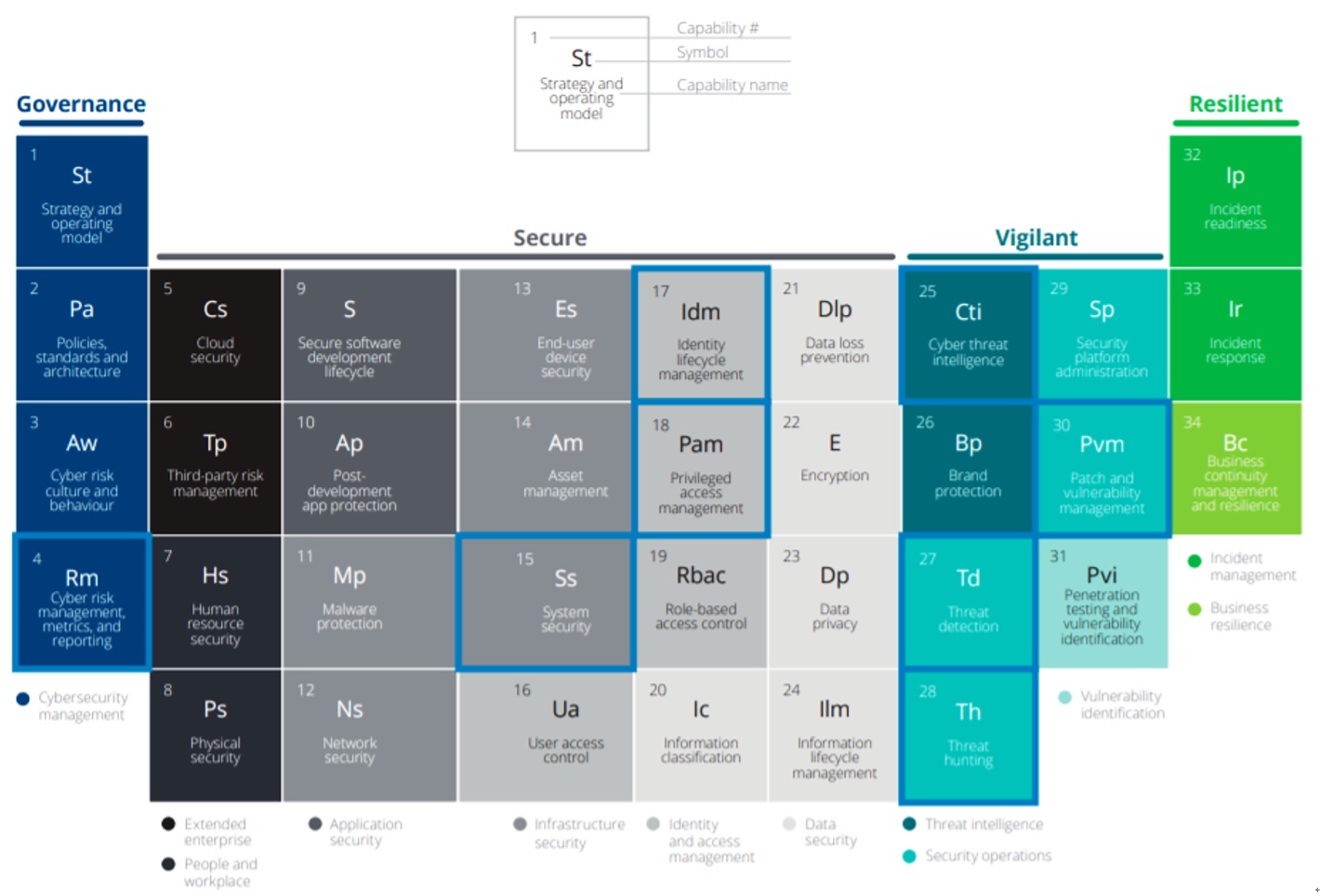
Figure 2: Where to apply AI technologies to improve your cybersecurity posture?
(Source: Deloitte – "Smart cyber: How AI can help manage cyber risk" [Note 2])
There are many compelling use cases where robotic automation (commonly known as Robotic Process Automation, or RPA), AI and other data analytics technologies help you prioritize your cybersecurity investment against AI-driven attacks.
Here we list some of the ways AI technologies can improve your security posture and enable earlier detection and response to any potential attacks.
With the help of automation, you can:
-
Governance, risk and compliance (GRC)
- Governance and risk management. Inform overall strategy and improve reporting capabilities by using large volumes of contextual data and decision points to help with strategic decision making that aligns with your organization’s risk appetite.
- Regulation synthesis and mapping. Develop and maintain the organization's integrated security controls framework, extracting information from multiple regulatory sources and guidelines.
- Assessment triggering. Conduct automated assessments periodically, or by changes to applications and/or business processes.
- Key Risk Indicator (KRI) automation. Automate the collection and visualization of KRI metrics to enable the organization to assess and address risk exposure.
- Responsibility allocation. Use self-service processes to allocate cybersecurity responsibilities across teams, improving efficiency and enabling closer alignment with risk owners.
- Control testing. Automate control testing so that it continually assesses control effectiveness and provides near real-time updates about the organization's security posture.
-
Identity and access management (IAM)
- Role maintenance. Use an AI engine to provide recommendations on role maintenance, helping organizations streamline the difficult, costly, and time-consuming task of keeping role definitions up-to-date.
- Role mining engine. Extend the AI role maintenance engine to mine roles from multiple data sources, recommending new roles and entitlements.
- Access request recommendation engine. Simplify the access request process by analyzing various data sources, such as peer group access and historical access requests, and then recommending the level of access required for a user.
- Access certification analytics. Analyze different data sets and apply analytics to improve the certification process by pre-approving certification items based on access request data, detecting anomalies in the attestation cycle, and using peer group data to calculate a confidence score that helps reviewers make informed decisions.
- Access usage data for analytics engine. Incorporate access usage data into the analytics engine to generate more informed and efficient insights.
With the help of AI and analytics technology, you can:
-
System security
- Control effectiveness. Augment and assess the effectiveness of tried and tested tools such as firewalls, proxies, and data loss prevention solutions by monitoring the available log data, then identifying and remediating misconfigurations.
-
Cyber threat intelligence (CTI)
- Cyber risk sensing. Follow the thought process of threat actors and discover the first sign of cyber attacks targeted at your organization before it happens by monitoring a wide range of public and closed intelligence sources such as hacker forums and private chat groups.
-
Threat detection
- Anomalous behavior detection. Help identify anomalous data access activity and malicious application activity by putting analytic focus on user logins, changes in user behavior, and unapproved changes.
- Threat discovery. Monitor activities and entities to establish normal behavior. The normal behavior pattern will then be used to detect sources of anomalies that could create potential risks such as fraud, money laundering, and insider threats.
- Alert cleansing and prioritization. Use machine learning to significantly automate the first level of triage based on factors such as type of attack, frequency, and previous experience.
- Targeted investigation and support. Use a big data platform to drive new insights through historical analysis, allowing investigations into incidents based on current and historical data to be done quickly and efficiently.
-
Threat hunting and vulnerability management
- Threat hunting. Quickly search for new threats by importing known tactics, techniques, procedures, and attack patterns, along with vulnerability details and remediation information, to help neutralize threats early in the attack cycle. This process must be continuous, integrated, and optimized to align with your organization's goals. Once a new threat is identified by CTI giving insight into the tactics, techniques, and procedures (TTP) utilized, threat hunters will then search for the identified behaviors in your environment with the help of defense analytics technology.
- Vulnerability scanning. Use bots to initiate and scan applications, systems, and other assets for vulnerabilities, assessing risk and prioritizing the patch schedule.
- Configuration review. Use bots to review system configurations to ensure baseline hardening and ensure no misconfigurations.
- Attack-path modelling. Perform predictive analytics on security data to determine vulnerable entry points and the likely path an attacker might use to gain access.
Summary
AI technologies have been getting a lot of buzz lately. While the AI technologies have become a potent part of cyber attacks, AI technologies and analytics can also lift your company’s cyber capabilities to the next level by giving you visibility on the threats and vulnerabilities in your environment, and proactively analyze where you can take actions to minimize your organization's attack surface. By taking the lead on applying these disruptive innovations to cybersecurity, you can tip the balance in your favor and stay a step ahead of the threats.
End notes:
- MIT Technology Review and Darktrace, "Preparing for AI-enabled cyberattacks" (2021).
- Deloitte, "Smart cyber: How AI can help manage cyber risk" (2019).